Network Analyzer Script – Deep Dive
Welcome to a deeper look into my Network Analyzer Script!
This Bash script automates essential network troubleshooting tasks by
combining some of the best open-source tools out there:
tcpdump, ping, traceroute,
dig, and nmap.
The goal? To simplify how sysadmins and engineers gather critical
information about network paths, DNS, open ports, and packet captures.
Everything is saved into a .txt report for quick reference
and a .pcap file for deeper analysis in tools like
Wireshark.
I created and tested this on MX Linux (Debian-based), but it should work on most Linux distros with minimal modifications, as long as the required packages are installed.
Video Demo
Why It’s Useful
- End-to-end diagnostics: checking connectivity, traceroute paths, DNS resolution, and open ports.
-
Real-time capture:
tcpdumprecords traffic related to your target, so you can see exactly what’s happening. - Easy reporting: The script spits out a text-based summary, plus the packet capture for advanced troubleshooting.
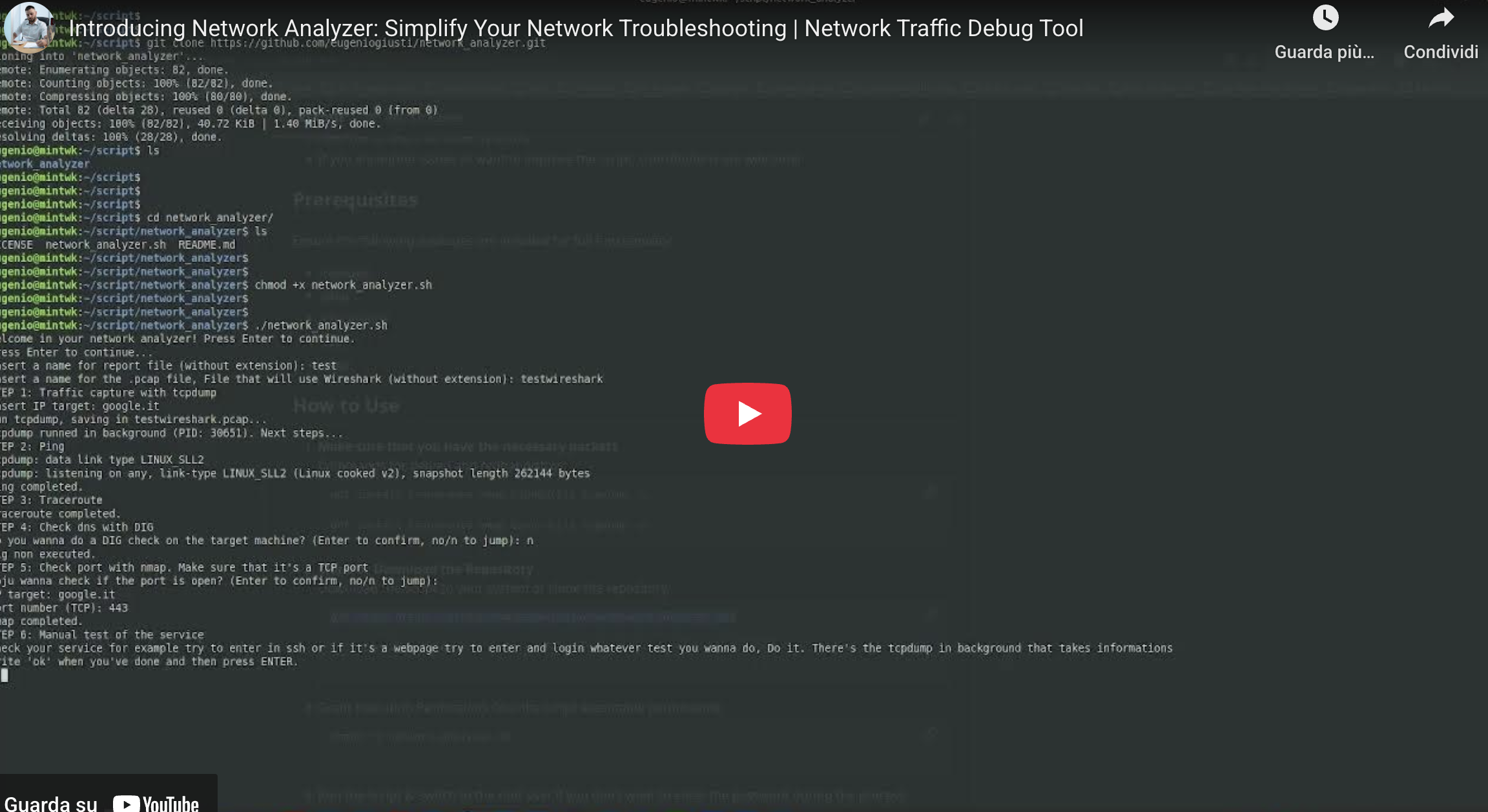
Usage Steps
-
Install dependencies:
tcpdump,ping,traceroute,dig,nmap. - Clone or download the repository from GitHub.
-
Make the script executable:
chmod +x network_analyzer.sh -
Run it:
./network_analyzer.sh <targetIP_or_domain> - Follow the prompts — the script will ask if you want to do a DNS check, port scan, etc.
-
Perform manual testing (like SSH or web login) while
tcpdumpis running.
Script Snippet
#!/bin/bash
# Step 1: Start tcpdump
sudo tcpdump -i any host "$target_ip" -w "$pcap_file" &
# Step 2: Ping
ping -c 10 "$target_ip"
# Step 3: Traceroute
traceroute "$target_ip"
# Step 4: Optional DIG check
...
# Step 5: Optional Nmap check
...
# Final: Stop tcpdump, save results in .txt + .pcapAdditional Insights
The script is intentionally interactive. After each stage, you can decide
whether or not to do the next step. You can also do manual
tests while the script is capturing traffic. For instance, if you
want to log in to a web application or run an SSH session to replicate
an issue, this traffic gets saved in the .pcap.
Once you’ve confirmed your tests, you type ok and press
ENTER, which stops tcpdump. The script then finalizes the
text report, kills the background capture, and you’re left with a concise
snapshot of what just happened in your network environment.